docker启动redis哨兵
1 | version: '3.8' |
1 | docker-compose up -d |

1 | version: '3.8' |
1 | docker-compose up -d |

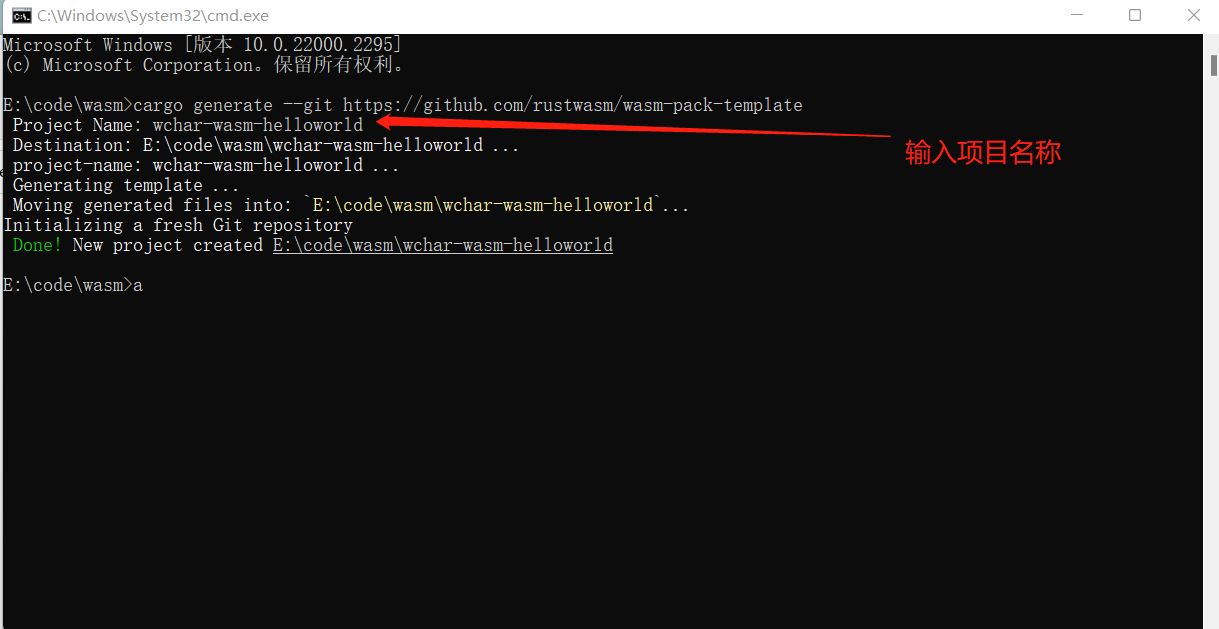
1 | cargo install wasm-pack |
1 | cargo generate --git https://github.com/rustwasm/wasm-pack-template |
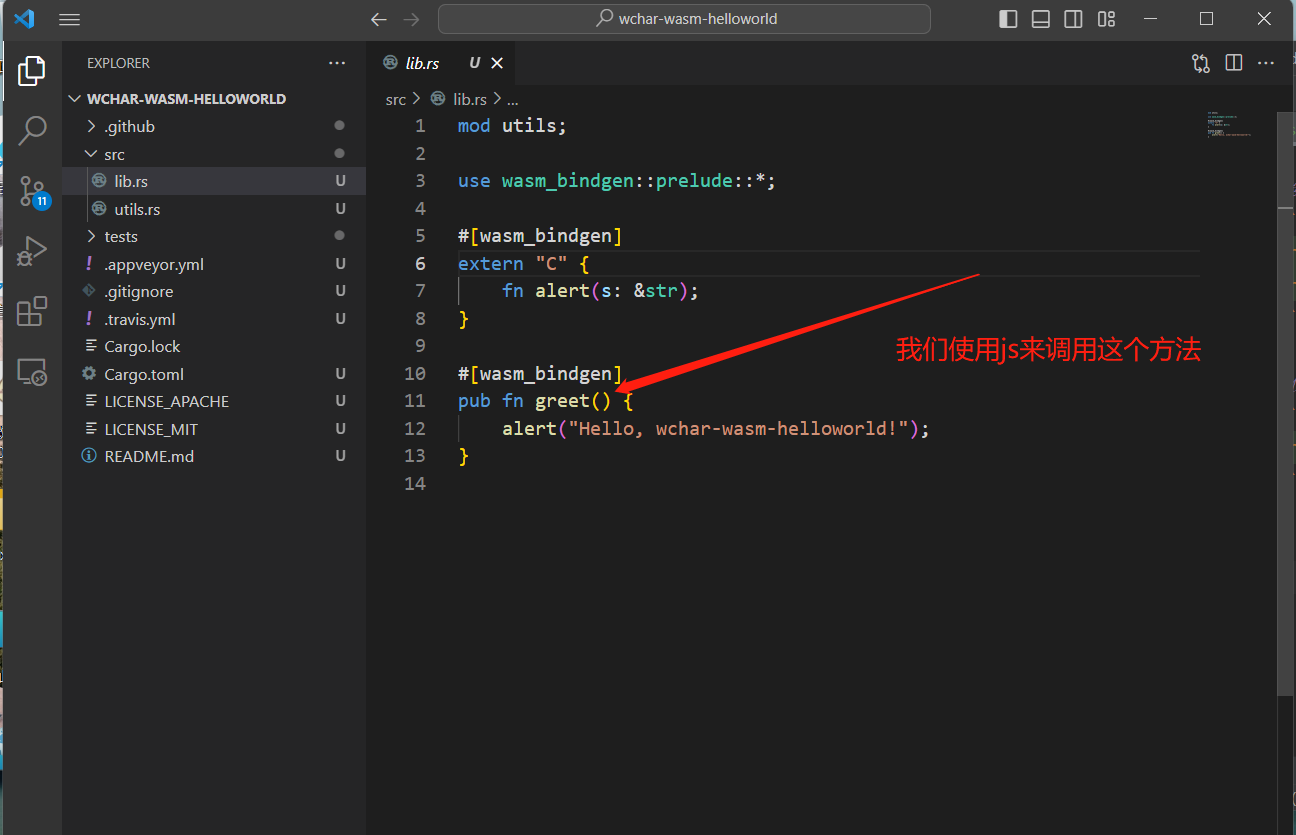
1 | wasm-pack build --target web |
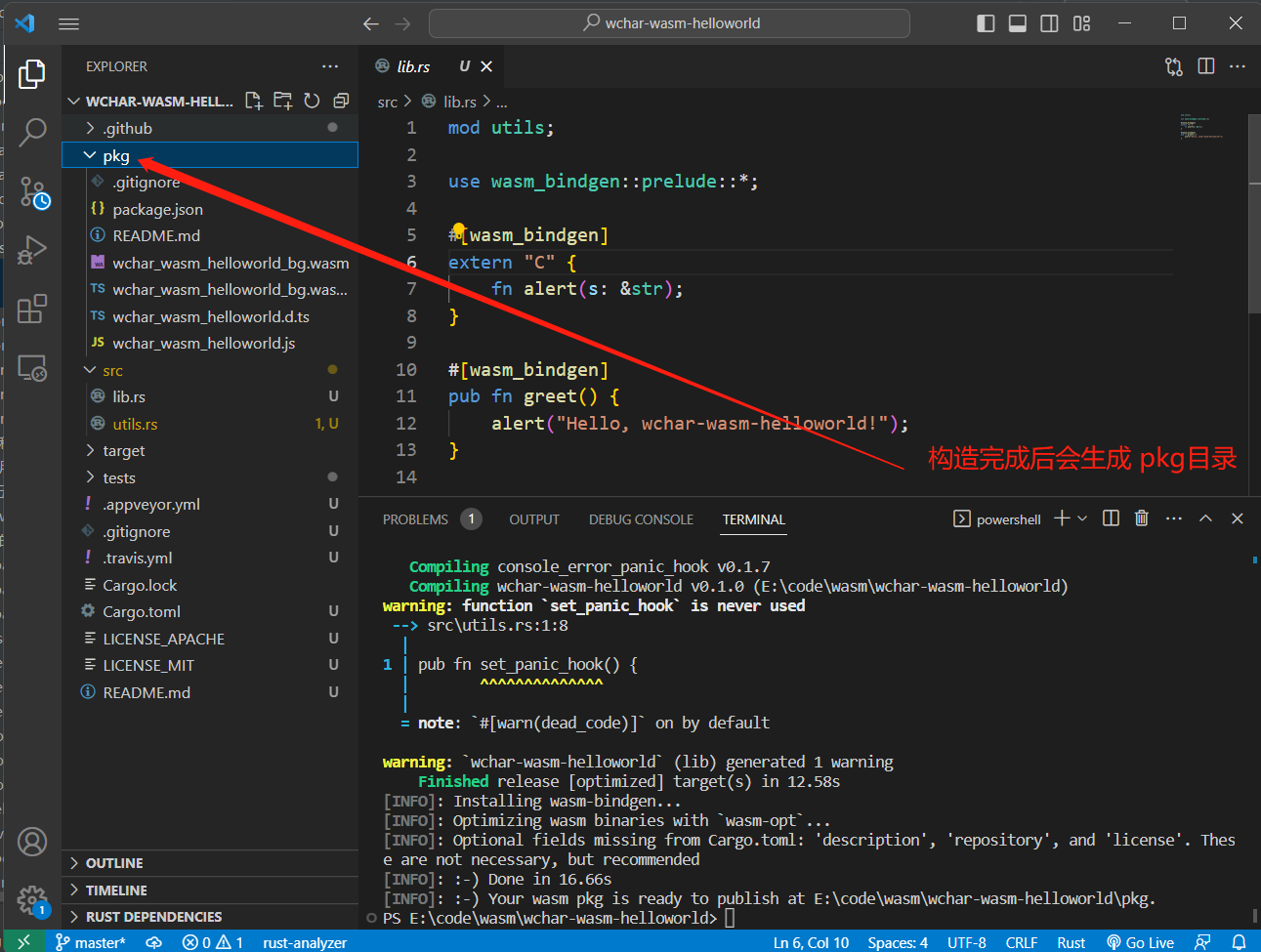
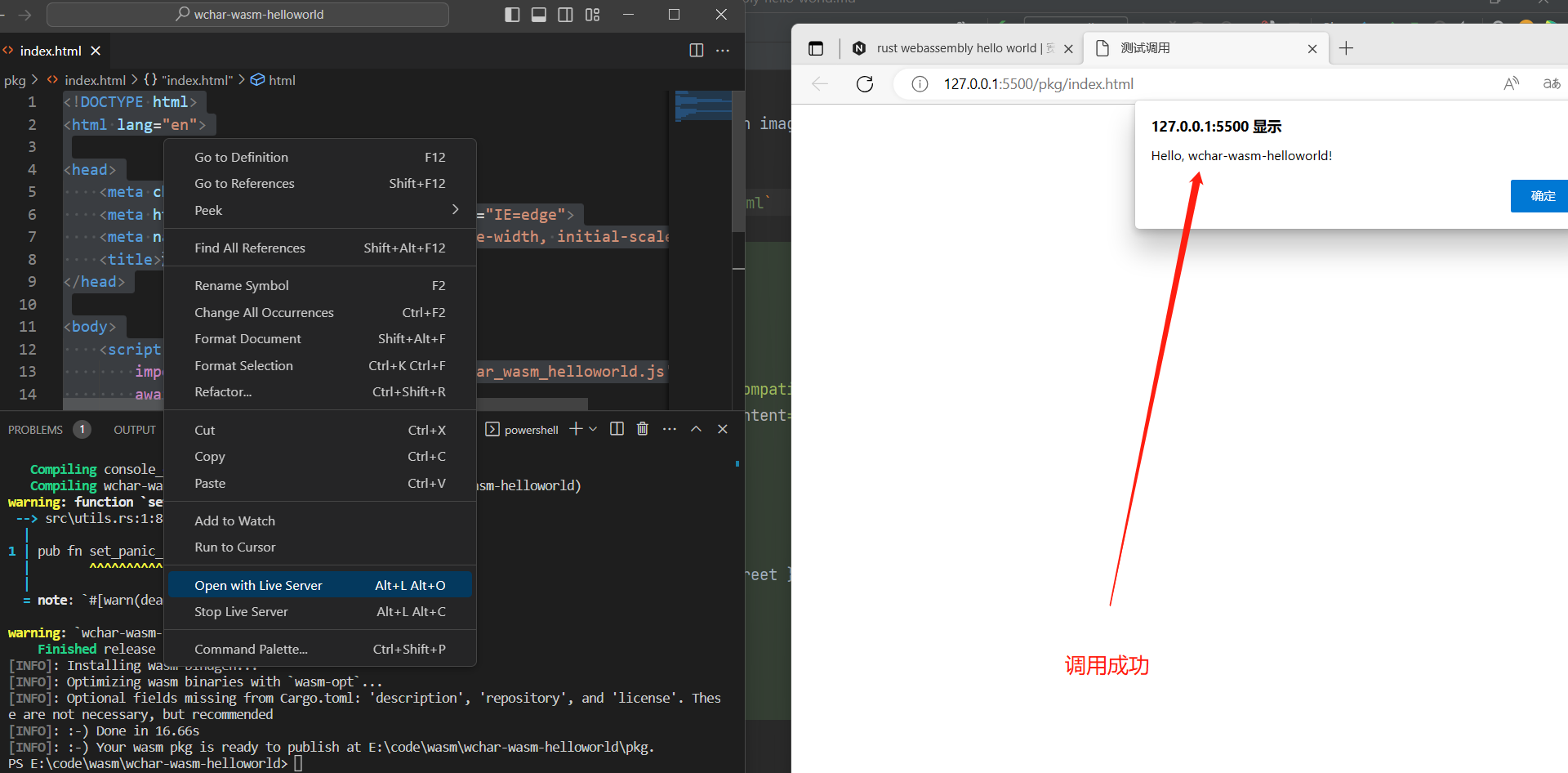
在 pkg 文件夹下新建 index.html
1 | <!DOCTYPE html> |
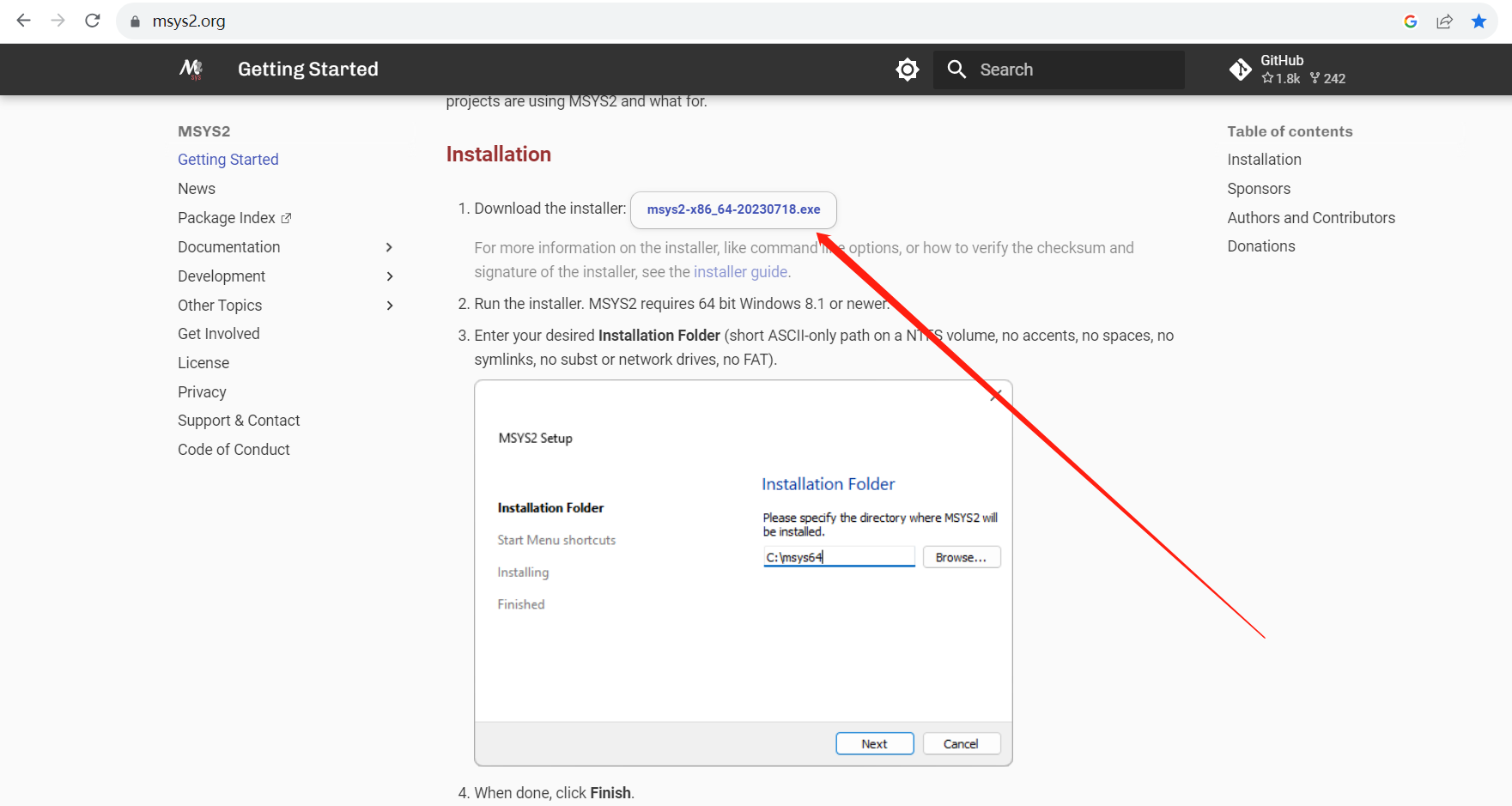
A.设置清华源
1 | sed -i "s#https\?://mirror.msys2.org/#https://mirrors.tuna.tsinghua.edu.cn/msys2/#g" /etc/pacman.d/mirrorlist* |
B.安装 mingw-w64
1 | pacman -S mingw-w64-ucrt-x86_64-toolchain |
C.添加环境变量
找到 msys2 安装位置下
1 | ucrt64/bin |
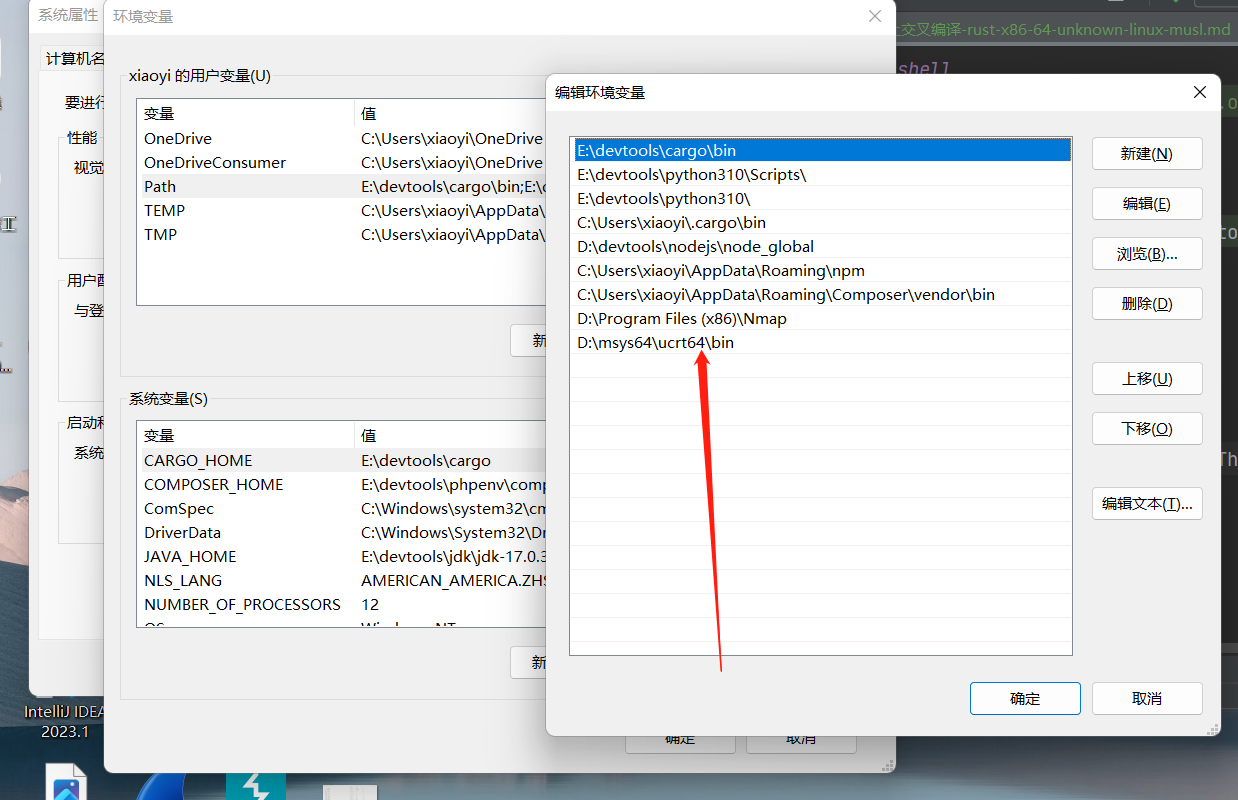
https://github.com/cross-rs/cross
1 | cargo install cross --git https://github.com/cross-rs/cross |
也可以直接下载 exe 二进制文件并添加到环境变量中
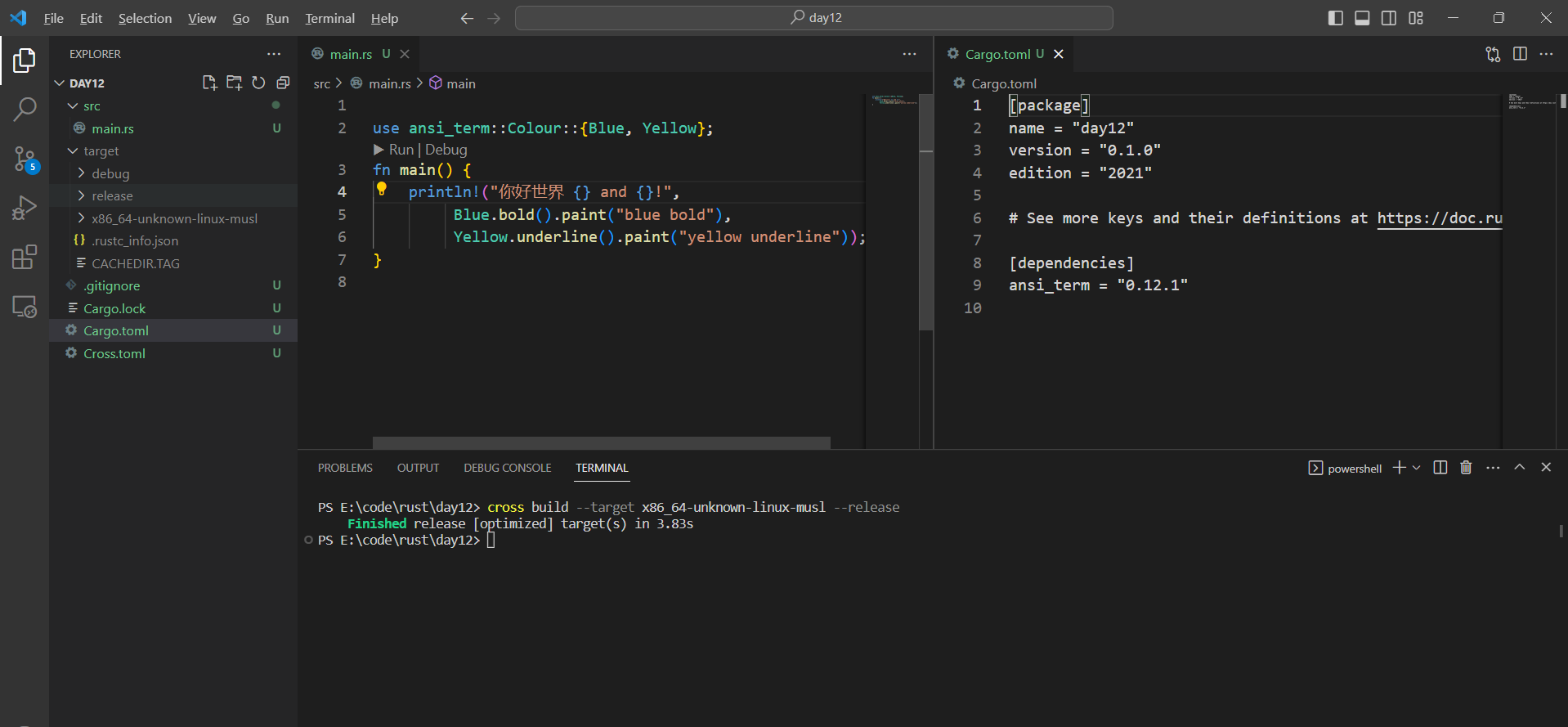
1 | rustup toolchain install stable-x86_64-pc-windows-gnu |
1 | cross build --target x86_64-unknown-linux-musl --release |
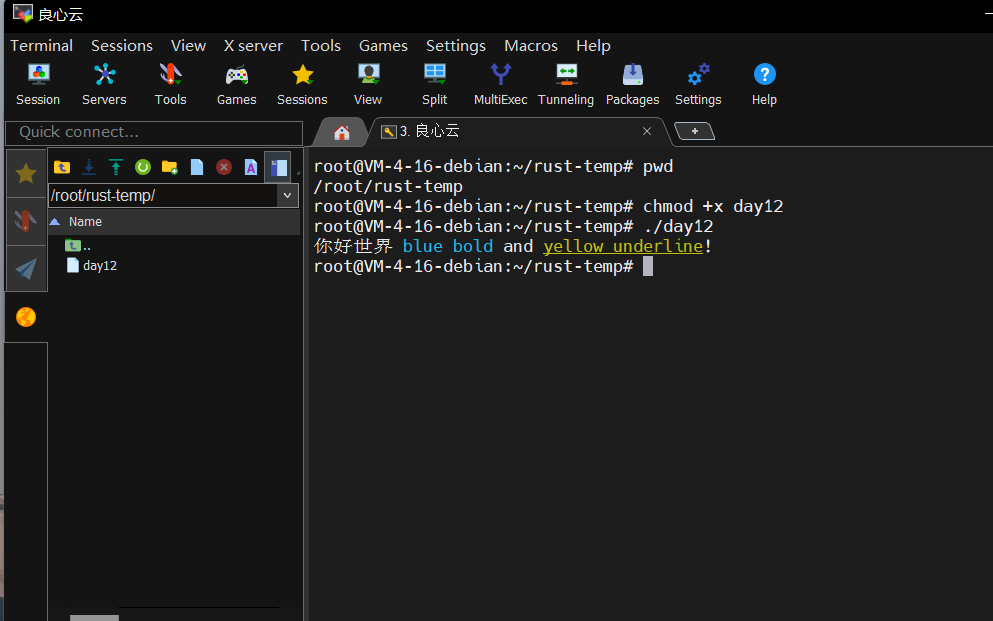
1 | --创建 dbname0628 数据库 |
1 | bool CanAccessFolder( LPCTSTR folderName, DWORD genericAccessRights ) |
本次博主将使用 c++ 操作 libcurl 进行 get post摘自官网: libcurl是一个免费且易于使用的客户端URL传输库,支持DICT、FILE、FTP、FTPS、GOPHER、GOPHERS、HTTP、HTTPS、IMAP、IMAPS、LDAP、LDAPS、MQTT、POP3、POP3S、RTMP、RTMPS、RTSP、SCP、SFTP、SMB、SMBS、SMTP、SMTPS、TELNET和TFTP。libcurl支持SSL证书、HTTP POST、HTTP PUT、FTP上载、基于HTTP表单的上载、代理、HTTP/2、HTTP/3、cookie、用户+密码身份验证(基本、摘要、NTLM、协商、Kerberos)、文件传输恢复、HTTP代理隧道等
本章节博主将使用 libcurl 完成 get post json post form 操作
夜深了 人也静了 来写一篇博文吧
此次博主介绍 cjson 这款类库的使用,博主用的是 vs2022
https://github.com/DaveGamble/cJSON
直接复制 cJSON.h cJSON.c 文件到项目中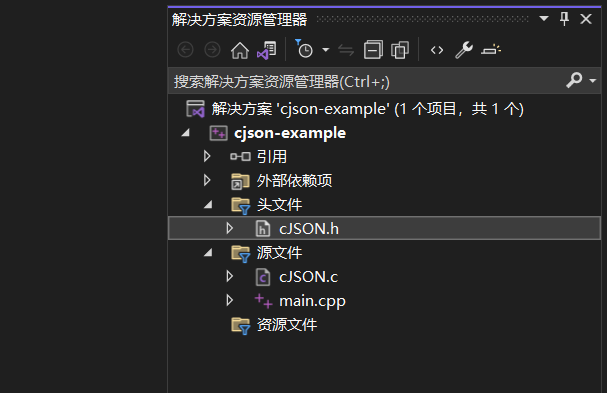
想为你的域名搭建权威DNS? 来试试 PowerDNS 吧
PowerDNS成立于20世纪90年代末,是开源DNS软件的主要供应商,本次博主将编写 PowerDNS 搭建教程
以及如何配置 PowerDNS-Admin 和 dnssec
DOH:
dns over https 查询和响应是加密的,但它们是通过HTTP或HTTP/2协议发送的,他一般在443端口运行
DOT:
dns over tls 是加密DNS查询以确保其安全和私有的标准,DoT使用安全协议TLS,它在853端口上运行